It is unrealistic to persuade a person to use a password longer than four characters and more complex than 4 digits, and even if it is possible, it will be written down on a monitor or piece of paper and hidden under a rug or keyboard. We don’t know how to be afraid, we think that the virus won’t get to us and no one needs our computer. But, alas, this is not so.
Dmitry Kets
It is unrealistic to persuade a person to use a password longer than four characters and more complex than 4 digits, and even if it is possible, it will be written down on a monitor or piece of paper and hidden under a rug or keyboard. We don’t know how to be afraid, we think that the virus won’t get to us and no one needs our computer. But, alas, this is not so. No matter what you say, 95% of the time only the person will be to blame.
Protecting your computer should start with installing the OS. Even if you install the OS on a clean computer ( hard drive does not contain any information) or the OS is already installed, do not skip this item. Have you ever thought about the installation process, namely the moment when hard drives crash? When you have a partition of, for example, 50 GB, you simply click the “Next” button, but if you delete this partition and create a new one, the system will inform you (see Fig. 1).

What is this system files and do you need them??? If you want to use Bitlocker, then definitely YES. Because the operating system boot loader will be written into a 100 MB partition, which, after starting the computer, will be able to decrypt the system disk (if there is one of the authentication methods TPM; TPM + PIN; TPM + PIN + USB key; TPM + USB key; USB key). The next important point in the installation process will be, oddly enough, the choice of network (if you are connected to it). I strongly recommend that you first set the location to “Public Network” (see Fig. 2).

Who knows what's going on on your network? Are you connected directly to the Internet or does your network consist of a small number of " clean, virus-free» computers?
The next stage of protection should be to determine user permissions. I am 99.9% sure that by reading this article you are in account a user with administrator rights. THIS IS WRONG!!! If you run a program, it has Administrator rights and can do ANYTHING, and it can ruin your system in just 1 double click, do you need it? You ask: “Am I a fool to run such programs??”, but on the Internet you again sit with administrator rights, and all downloaded programs are launched with administrator rights, and who guarantees that there are no viruses? Or a friend came with a flash drive that had been somewhere unknown and contained Conficker, also known as Kido. That's the end: the system is infected. Yes, UAC will try to warn you, but, again, I am 80% sure that you have disabled it, and the remaining 19.9% simply do not know how to do it, and always click “Yes” without reading what is written there. But still, let's return to the users. It’s good if you work alone at the computer. But what if you have a family and have at least two or three accounts? At the same time, everyone should have limited rights and opportunities. The account editor will come to the rescue:
Start → Computer (“right-click”, Control) → Utilities → Local users and groups → users(see Fig. 3).

Next, create the users you need using the Action menu → New user(all new accounts are included only in the Users group). Specify the user data and, if the user does not need a password to log in, uncheck the “Require password change...” checkbox. Then enable the built-in Administrator account and set a password for it. Select Administrator → right-click, set a password (enter a password at least 8 characters long, containing numbers, special characters, upper and lowercase letters). Again, select Administrator → right-click, Properties and uncheck “Disable account”. Next, determine which groups your users will belong to. I recommend assigning groups depending on the needs and experience of the users. Do NOT add the user to the Administrators group.
Select the user → right-click, Properties → go to the Group Membership tab → Add → Advanced → Search. Highlight necessary groups and click OK (see Figure 4).

That's all the preparation of users, now when you log in you will see the accounts you created.
You probably have a question: “So, now, to install any application, I will have to log in as an Administrator?” The answer is clearly no. If you want to run an application that requires administrator rights, the system will warn you and offer to run this program under an account that has administrator rights. It will also describe what kind of program requires such rights, who its publisher is and where it is launched from (see Fig. 5).

Since until this time no third-party software was installed on the new OS, even now your computer is susceptible to the possibility of infection. This can be prevented very easily by following two steps, such as: install latest updates and also install antivirus program. I think there’s no point in telling why updates are needed (BlackEdition-OS users don’t count). But about the “Support Center” it makes sense. I think that a “checkbox,” most likely with a cross, on the taskbar has already attracted your attention more than once. This is the "Support Center", which brings together a stream of messages from the main Windows maintenance and security functions.
After Windows installations 7 in the support center there will be two problems related to updating the OS and the lack of protection against viruses (antivirus software) (see Fig. 6).

It's been half a year since the licensed OS (from Windows XP to Windows 7) became absolutely accessible to all users. free antivirus Microsoft Essentials. No matter what negative things they say about it, BUT not a single free antivirus in the month of its existence has yet made it into the TOP 10 (link to the original document, in English) of the best antivirus solutions for the home (in which, by the way, the rest are all paid), with while working steadily and with dignity. Today, for it to work fully, you must have a licensed activated OS, as well as Internet access to download the signature database. By the way, anti-virus signature databases are also available in Off-Line mode. They can be found here (x86 and x64). The antivirus itself can be (and I believe it should be downloaded from the official website, for THIS reason) at this address www.microsoft.com/security_essentials . During installation, the antivirus will check your system for authenticity and, as confirmation of a successful check, will display the message “This copy of Windows has been authenticated." (see Fig. 7).

Also, it should be taken into account that authentication takes place on-line.
After installation, the antivirus will connect to the update server and download the signature database (approximately 70 MB). After completing these steps, your computer is ready to surf the Internet and install additional software.
After installing the system, the “Public Network” network location was selected, which allows you to protect your computer as much as possible, but also significantly limits your freedom of action, such as detecting your PC on the network, as well as providing access to files over the network. Therefore, to configure the network, find the network connection icon on the taskbar and, by clicking on it, select “Network and Sharing Center”. In the window that opens, select and click on the “Public Network” message (see Fig. 8).

After which you will be presented with a choice of location of your computer on the network. Such as: “Home network”, “Enterprise network” and “Public network”. Each of these networks has its own characteristics and when you select one of them, Windows will be automatically configured to work on that network. Now in more detail about each type of network connection.
Home network - for use on home networks or networks whose users and devices are known and can be trusted. Computers home network may belong to a home group. For home networks, network discovery is enabled, allowing other computers and devices connected to the network to be used and allowing other users to access the computer from the network.
Enterprise network – for working in the network of a small office or other workplace. Network discovery, which lets you use other computers and devices connected to your network and allows others to access your computer from the network, is turned on by default, but you can't create or join a homegroup.
Public network – for networks in public places (such as cafes and airports). This network location is configured in such a way as to make the computer “invisible” to other users and increase its protection from malicious software from the Internet. Homegroup is not available on public networks, and network discovery is disabled. This option should also be selected if you are using a direct Internet connection without a router or a mobile broadband connection.
I believe that the home network is relevant, as is the protection of personal information within its perimeter. First, switch to “home network” mode. After which you will be given the opportunity to select resources to which you can provide access (see Fig. 9).

After you select the resources to which you want to provide access and click “Next,” the system itself will configure everything and generate a password for you that can be provided to members of your home network to connect their computers to it. Thus, you are the initiator of the home network, which will allow you to exchange information within its aisles. The system generates it, taking into account all the complexity requirements (presence of large and small letters, numbers, special characters). You probably have a question: what to do if the computer that initiated the network is turned off? What will happen to the network?
It's simple: any client connected to your network (using a password) can take over the role of a server (there can only be one server on the network), which makes it easy to use. Please note that only happy owners of Windows7 can participate in such a network, and versions of Windows7 OS “Start” and “Home Basic” can only act as clients. If you need to reconfigure or, for example, change something on your home network, this is quite easy to do. To do this, you must go to the “Network and Sharing Center” and then go to “Select a home group and settings public access", where you can also change the network access password. For example, if you find it difficult to remember the password generated by Windows7, you can easily change it to any other one.
Well, it's time to sum up all the work done.
- The system is installed correctly, with bootloader features.
- Delegation of rights in the system is configured.
- Updates and antivirus are installed.
- Computer protection is independent of network location.
- And something else...
Definitely, you have a question: what is the author talking about? The answer is simple: we have set up the system, but what will you do if it crashes? Just don’t throw stones towards 7, no, it won’t fall that easily, you just haven’t read to the end yet.
The system is more likely to crash due to YOUR actions, namely from installing incompatible software. For example, old versions of Alcohol 120% or NERO, which most often led to system crashes and blue screen. This can be prevented very simply. By creating BackUP system disk or files you select. Just don’t, after these lines, immediately go to torrent networks or something similar and look for the latest build of Acronis or Ghost there. Everything is much simpler: this solution already exists and it is integrated into the system. The main advantage is working in background OS, which will allow you to create BackUP data without rebooting. Also, at any time you can restore all information or perform selective file recovery. You can find this utility in this way: Start - All Programs - Maintenance - Backup and Restore. In the window that opens, select “Create a system image”, which is, in fact, the same BackUP. To start you will need administrator rights. Next, the system will prompt you to specify the location of the system image (see Fig. 10).

There are three options available in the list, each of which has its own pros and cons. Let's look at each option.
On your hard drive. Today, most users have computers with one hard drive, but there are also users who use two hard drives, connecting them in a RAID 0 array, which almost doubles the speed of information exchange, but at the same time puts the safety of all data at risk , since if one of the hard drives fails, it will be almost impossible to recover the data (this will most likely exceed the cost of the information itself). But, still, if you have two hard drives that are not connected to each other, then this option is just for you. You can also store a system image on one hard drive (on different logical drives C, D), but if the hard drive crashes, it will be impossible to restore the system.
On DVD -disks. This is quite a good option, but it is worth considering the sufficient quality of the disks so that information can be stored there for several years without damage, as well as the location and quality of storage of these disks. Also, the disadvantage is the inability to create system images on a schedule. But if you need to make one backup copy your system and disks will be stored in a safe place, then this method is just for you.
In a network location. Enough interesting way storing system images is more likely to be used in companies, because you will need a file server that will provide reliable data storage and high performance. And also, you should not forget about the load on the network itself.
Your only choice is which option you will use.
For myself, I decided to keep system images on the hard drive, because my laptop is limited to one such drive. After completing these 5 points, you will ensure decent protection and system stability.
Safe company - efficient company. This is an axiom for global business. One of the most important components of ensuring production safety is the ability to assess existing risks and make effective decisions to minimize them
A person risks every day, hour, minute, second of his life. This is not an exaggeration. Even a simple trip to the cinema threatens us with misfortunes - from a minor injury from falling down the stairs to death as a result of a traffic accident. What can we say about working in the kitchen or workshop. However, accidents rarely occur. The thing is that every second we assess the impending danger, immediately develop ways to reduce the risk (usually to zero), implement the decisions made... and ultimately remain safe and sound.
In principle, this is a risk management model that works in the same way in any company or industrial enterprise. Only business has to deal with an incomparably large number of inputs, and the cost of an erroneous decision can be calculated in colossal sums, environmental disasters and sometimes human lives. Therefore, progressive companies pay the closest attention to building a risk management system in the field of industrial safety. Gazprom Neft is also actively involved in this work.
Risks by ranking
In order to talk about risk management, it is worth understanding what risk actually is. There are many definitions, and each official document regulating this area in one way or another gives its own. “Risk is a consequence of the influence of uncertainty on the achievement of set goals” - this is, for example, the GOST R 51897–2011 standard “Risk Management. Terms and definitions". And this is Federal Law-184 “On Technical Regulation”: “Risk is the probability of harm to the life or health of citizens, the property of individuals or legal entities, state or municipal property, the environment, the life and health of animals and plants, taking into account the severity of this harm.” Gazprom Neft has adopted and enshrined in the company standard the following formulation: “The occurrence of an undesirable event, a combination of the likelihood of a hazardous event or impact and the severity (injury or impairment of health, damage to the environment and property) that may be caused by such an event or impact.” .
Let us make a reservation that we are talking only about risks in the field of industrial and environmental safety, labor protection and civil protection (HSE risks), since there are a huge number of other types of dangers and uncertainties - financial, investment, organizational, and so on.
Risks associated with the human factor can only be reduced by changing behavioral patterns
In turn, HSE risks are divided into two large groups: professional and technogenic. The first are caused by the impact of harmful or dangerous production factors on the employee during the performance of his duties. For example, the possibility that a person working at height may fall down is an occupational hazard. Technogenic risks - the dangers that production technologies bring with them - can affect the entire society. “According to international statistics, the frequency of occurrence of professional risks is much higher than technological ones, but the consequences of incidents associated with this category are much lighter,” said Oleg Nikolaenko, head of the industrial and environmental safety department at Gazprom Neft.
A scheme for ranking the consequences of incidents according to their severity is unlikely to be significant for a person who finds himself in the role of a victim, but it is extremely important for building a competent risk management system. For example, as practice shows, significant damage to the company’s economy is caused by loss of ability to work by employees, emergency failure of equipment, and damage to property.
Human factor
The notorious human factor is the cause of the vast majority of industrial accidents. The roots of this group of risks lie primarily in human psychology, which is why they are leveled with the help of technologies for changing people’s behavioral patterns, supported by various training programs. That is, in general, we are talking about the transformation of corporate culture.
“The transformation of culture is a long process, but it is a path that must be followed,” noted Tatyana Yurchenkova, head of personnel training, competency development, and safety culture at Gazprom Neft. - Today, safety has become the main corporate value of the company, and we try to convey to everyone that preserving life and health is more important than solving any production problems. We must teach employees to correctly assess risks in order to prevent incidents from occurring, but at the same time not to cause damage to the company through unjustified production stops.”
It was this task that formed the basis of the solution called “5 steps,” which allows a person to competently assess the situation, and he must do this every day. In order for a technique to become a rule of life, it, according to Oleg Nikolaenko, must be simple and logical: “Our problem is that we explain simple things to people in too much difficulty. When a person hears such formulations as “risk assessment, risk management,” he automatically forms the idea that these are some complex processes that require special knowledge. Now we deliberately simplify the instructions, offering simple and understandable tools, such as “5 steps”. With their help, we simply tell everyone: stop five steps before the production facility, think about what dangers you face in connection with performing a specific job, what you must do to prevent the danger from becoming a real incident, what you will do if changes will occur in the process."
However, the matter, of course, is not limited to just changing the psychology of people. The likelihood of risks associated with the human factor being realized is reduced by various organizational measures. For example, the system of access to work excludes people who do not have the necessary competencies to perform it or who have not undergone the appropriate training. Beginners should pay special attention. And the use of modern personal protective equipment is designed to reduce the severity of the consequences of incidents if they do happen.

Elena Ilyukhina,
Deputy General Director of Gazprom Neft for Legal and Corporate Issues:
All aspects of production involve risks. Process safety risk management begins with the assessment and design of new facilities and does not end until they are decommissioned. Each employee must be able to assess risks to life, consequences for assets and the environment, and organize work for themselves and their subordinates in such a way as to mitigate them.

At the same time, we should not forget that most of the work directly related to production, and therefore with increased danger, in the oil industry is traditionally carried out by contracting organizations. This means that risks must also be controlled on the side of counterparties. Today, Gazprom Neft is actively introducing new approaches to relationships with contractors, covering the entire perimeter of contractual relations, from selection to evaluation of completed work. And in many ways, the success of the partnership depends on the quality of the counterparty company’s risk management system, its level of maturity in the field of HSE and its willingness to change in accordance with Gazprom Neft safety standards.
People and machines
Technological risks are no longer psychology. The directions for their reduction lie primarily in the areas of organization, design, analysis, and statistics. Moreover, solutions that ensure maximum safety, taking into account all the nuances, should be laid down at a very early stage, when process facilities are just being designed, and cover their entire life cycle, right up to dismantling and disposal. All world industrial leaders do this, and it is this concept that Gazprom Neft also uses in its projects today. A striking example is the new Arctic fields, which are now being put into operation one after another.
"Five Steps"

Moreover, several years ago the company became a pioneer in this direction, together with the Russian Union of Industrialists and Entrepreneurs, initiating at the legislative level the introduction of a risk-based approach into the processes of design, construction and operation of industrial facilities.
“Through an open government, we have made changes to Federal Law 116 “On industrial safety of an organizational nature. For example, the system of access to work excludes people who do not have the necessary competencies to perform it or who have not undergone the appropriate training. Beginners should pay special attention. And the use of modern personal protective equipment is designed to reduce the severity of the consequences of incidents if they do happen.”
Determining the level of risk

Risk management system in the world
oil and gas companies

At the design stage, almost 90% of technological risks are leveled out or reduced to the lowest possible residual level. However, even at the stage of operation of facilities, there are many risk management tools - from conducting acceptance tests to using modern systems control of technological parameters, equipment diagnostics, implementation of progressive schemes for planning and carrying out repairs. A large layer of this work is included in one of the independent areas of development of the Gazprom Neft operational management system -.
However, it is obvious that decisions made within the risk management system, especially those related to minimizing man-made hazards, are often quite resource-intensive. Therefore, one of the large-scale initiatives in this area that the company is implementing today is linking the risk management system with budgeting. “We must clearly show a tool for assessing the possible consequences of undesirable events, their likelihood, and the effectiveness of the measures taken,” explained the head of the industrial safety department at Gazprom Neft. “In addition to updating assessment tools, the initiative will determine the procedure for budgeting the necessary funds based on identifying and ranking HSE risks to reduce them to an acceptable level, and also introduce an environmental risk management system.”
By the way, it was precisely the insufficient connection between the risk management and budgeting processes that the experts who carried out diagnostics of the HSE management system at Gazprom Neft identified as one of the important identified shortcomings. And this is really important, since underestimation and, therefore, underfunding of the risk reduction program can lead to an increase in the number and severity of the consequences of incidents. In turn, excessive investments, worsening the economics of projects, will not bring benefits. This is exactly what the ALARP* principle says: risk mitigation measures should be intensified until the costs (organizational, financial and time) begin to increase significantly without creating significant additional benefits (which makes these additional measures unreasonable and impractical).

Alexey Yankevich,
Deputy General Director of Gazprom Neft for Economics and Finance:
Every manager must understand that by devoting time and resources to safety risk management, they are investing in the future of the company. In the long run, industrial safety is good business.
In general, the experts came to the conclusion that a high-quality approach to risk management exists at Gazprom Neft, but the risk management system is not fully implemented into the company’s operating activities. Obviously, the solution to this problem largely lies in the field of management. People key to business and production must themselves have sufficient competencies to effectively manage risks - only in this case every technological and professional decision will be justified. Training such decision makers at all levels, from foreman to senior managers, has become a separate initiative as part of the process of building a risk assessment and management system at Gazprom Neft.
This system is the cornerstone of industrial safety, the level of development of which, in turn, largely determines the efficiency of the entire business.
 The competence of specialists at all levels is the key to compliance with industrial safety rules
The competence of specialists at all levels is the key to compliance with industrial safety rules
*ALARP principle (as low as reasonably practical) is a principle that determines the minimum acceptable level of risk
1. Do not carry out any work without a written work order, an authorization order when performing high-risk work.
2. Do not enter or start working in mine workings in the absence of fastenings and in the presence of dangerous overhangs of pieces of rock mass until the mine workings are brought to a safe condition.
3. Do not enter the drilling and blasting area.
4. When working at height, use personal protective equipment and insurance, fence off the danger zone to avoid falling objects and injuring people.
5. When performing work, use serviceable and certified personal and collective protective equipment.
6. Do not stand or perform work under suspended loads when operating lifting mechanisms.
7. Do not approach moving or operating vehicles until the vehicle has come to a complete stop and contact has been established with the driver.
8. Repair and maintenance work with any type of energy (electric, compressed air, steam, water, etc.) should be carried out using blocking devices.
9. Follow the established route to and from the workplace. Do not enter the exhausted workings during underground work.
10. When performing work, use proper equipment and tools.
Five security steps:
1. Do I understand my task order? Do I understand all the risks involved?
2.Is my route to my workplace safe?
3.All my tools are in good working order. All my equipment and fixtures are in good working order.
4. My workplace is safe.
5.I am aware of all the work going on around my workplace.
2 Health and safety requirements before starting work
2.1 Foreman of the section (shift) of the MPC PU:
Conducts “hazard identification and risk assessment” at each workplace and eliminates identified risks;
Issues a work order - a task for the smelters of the MPC control center to carry out work at the PV;
Familiarizes employees with incoming documents (newsletters, telephone messages, messages, orders, instructions on the MPC);
Checks the medical examination book of registered employees;
Checks the pre-shift medical examination (alcotest) of overhead crane operators and the electrician on duty;
Introduces the register of risks of possible injury;
Surveys employees on their knowledge of 10 k.p.b. and 5 sh.b., security policies, orders issued by the BMZ, orders issued by the MPC;
Checks the availability of PPE for workers;
2.2. Before starting work, workers must:
Pass a medical examination for those registered or undergo a pre-shift medical examination (alcotest);
View special clothing, which must be in good condition, fastened with all buttons;
It is mandatory to have personal protective equipment, i.e. a helmet, mittens, a respirator, earplugs, a cloth jacket, cloth trousers and a protective shield;
Receive a written work order - an assignment to carry out work in accordance with these instructions;
Familiarize yourself with incoming documents (newsletters, telephone messages, messages, orders, instructions on the MPC);
Familiarize yourself with the register of risks of possible injury;
Know 10 k.p.b. and 5 sh.b., security policy, orders issued by the BMZ, orders issued by the MPC;
Use PPE in accordance with industry standards specified in the work instructions for the professions of PU MPC;
If a risk of possible injury is identified, the employee fills out signal sheet located at the site (shift) foreman of the MPC PU, having notified the site’s engineering and technical personnel, put signal sheet in the box provided for this purpose.
If a danger of causing a threat to the life or health of workers is identified, it is necessary to fill out employee refusal form and hand over to the foreman of the section (shift) of the MPC PU, then, until the inconsistencies are eliminated at the workplace, receive another written order - an assignment from the foreman of the section (shift) of the PU MPC;
Before starting work, it is imperative to make sure that there are no unauthorized persons in the smelters’ work area;
Check the serviceability of the tools;
Check the sufficiency and correctness of safety measures for TB;
Familiarize yourself with the condition of the equipment, the moving parts of the units should be protected, but should not impede the filling process of the previous shift, paying special attention to quality and performance;
In winter, make sure there is no ice on the sites;
Use (times) anti-slip agents;
Reliability of fastening and serviceability of fences;
Check the cleanliness of the workplace;
Check the serviceability of the sound and light alarm;
Check the lighting of the workplace;
Check the supply of refractory clay and plugs;
Operation of ventilation devices;
Lack of dampness and fuel oil on working areas near the furnaces.
2.3 General fire safety requirements:
For fire safety purposes, workplaces in the workshop are equipped with shields with fire extinguishing equipment;
Free access to fire extinguishing means must be ensured;
It is prohibited to bring matches, lighters, lanterns and other sources of fire into explosion and fire hazardous areas;
Smoking strictly in certain places;
The use of fire-fighting equipment and inventory for production and other needs not related to fire-fighting is prohibited;
2.3.1 Employee actions in case of fire:
In the room where the fire broke out, drafts must not be created, since the influx of fresh air only intensifies the combustion, so windows and doors in this room should be closed;
Opening windows and doors is only possible to save people, evacuate material assets, and extinguish a fire. To prevent the spread of fire, if it has just begun, it is necessary to immediately turn on the ventilation in the room and shut off the gas, oil, gasoline, and oil pipelines.
When leaving a burning room, you must not create turmoil and panic, maintain calm and order, which will ensure a successful evacuation.
To make breathing easier, cover your nose and mouth with a handkerchief moistened with water;
Each employee of the MPC is obliged, in case of detection of a fire, to report this to the fire department, inform the shift foreman and then begin to extinguish the fire with primary fire extinguishing means;
There is a single fire brigade call number “101”;
At BMZ, in addition to this number, you can call the fire brigade by calling “4-75-11”.
2.4 Characteristics of work:
Maintenance of furnaces and outlets when releasing the melt, monitoring their condition, the condition of siphons, tuyeres, caissons, chutes and other equipment;
Washing and cleaning the bathtub from deposits;
Adjusting the height of melting products in the siphon;
Control of copper content in slag and matte;
Release of slag and matte;
Maintenance of auxiliary equipment;
Inspection, cleaning of tuyeres and tapholes, monitoring their operation, blasting mode, level of slag and melt in the furnaces;
Replacement of tapholes;
Cleaning the workplace;
Regulation of the position of the electrodes of electric furnaces, the temperature or intensity of the combustion process, and the flow of water into the caissons;
Signaling for slag release;
Preparation of gutters, slag bowls and preparation of refractory materials;
Participation in cleaning loading and slag windows, thresholds;
Slinging boxes;
Release of slag, matte, filling of outlets, slag windows, sills, gutters, cutting and sealing of tapholes, replacement of the hole plate, settling tanks, molds and bypass of electrodes under the guidance of a more highly qualified smelter;
Preparing the heel.
Determination of suitability for work, drying, heating and cleaning of molds, ladles, chutes;
Installation, removal and cleaning of spray nozzles;
The accident at the Raspadskaya mine, which killed 66 people, and the subsequent accident at the Alekseevskaya mine in the city of Leninsk-Kuznetsky, it seems, will still lead to the long-awaited tightening of labor safety requirements at Russian mining enterprises. The outlines of the new order have so far been drawn in general view. What needs to be done?
An American non-governmental organization specializing in environmental, energy and minerals research, studied the development of the coal mining industry in the United States from the 1930s to the 1990s. During this time, the number of injuries per unit of time worked decreased in the United States by approximately 2.6 times, and the number of deaths by 7 times. The study plans five basic steps that made it possible to achieve this result. In recent years, in Russia, the mortality rate in mines is on average three times higher than in the United States, and in some years it was more than six times higher than the American one, despite the fact that the number of people employed in the coal industry in both countries is almost the same (133,400 in America and 164,800 people in Russia, according to data for 2009).
Mortality in coal mines in Russia and the USA
Russia USA
Source: Rostekhnadzor, Mine Safety and Health AdministrationWhich of the measures taken in the United States is Russia implementing and how successful is this process?
Creation of a body monitoring safety in mines
As Vladimir Putin said at a video conference on Monday, a separate Mining Supervision will be created in Russia within the structure of Rostekhnadzor, which will deal exclusively with safety issues in the field of mining. Its American counterpart, the Mine Safety and Health Administration (MSHA), appeared back in 1977, immediately after the adoption of the Federal Mine Safety and Health Act.
The reason for the adoption of this law was a series of accidents in US mines with a large number of victims. The new administration, whose inspectors inspect each mine at least four times a year, and open pits at least twice, received the right to issue fines for any violations of safety rules, demand compliance with its own regulations, and seek the elimination of detected violations at mining enterprises of any form of ownership. Since the formation of MSHA, mortality in US mines and strip mines has decreased by approximately four times.
In Russia, the entire Rostechnadzor is still a structural unit of the Ministry of Natural Resources, but soon it will be transformed into an independent organization with direct subordination to the government of the Russian Federation. This will raise his status and increase his ability to influence the owners of mines and open-pit mines, hopes the head of Rosugleprof, Ivan Mokhnachuk. “I know of cases when the leadership of Rostechnadzor made a decision to tighten some things in relation to mining enterprises, and the minister later canceled it. Why, who came to him, what they brought, I don’t know,” says Mokhnachuk.
The right of inspectors to stop the operation of a mine
MSHA has the right to suspend the operation of a mine - but only if the enterprise is unable to pay fines issued or refuses to cooperate with the administration. The need to increase MSHA's authority in this area is also felt in the United States.
On April 5, 2010, a methane gas explosion occurred at the Upper Big Brunch mine in West Virginia, killing 29 miners and becoming the worst disaster to hit the U.S. coal industry in 40 years. In recent years, the mine has been caught hundreds of times in violation of safety regulations: in 2008, MSHA inspectors recorded 197 such violations, in 2009 - 501, in the first three months of 2010 - 124. The owner of the mine, Massey Energy Co., was constantly fined - so , in 2009 the total amount of fines was almost $900,000, and in total Massey Energy, which owns 56 mines in the United States, was fined $13 million last year. But the company fought most of the fines in court and continued to operate.
Disasters in Russian coal mines in recent years have been even more widespread - an explosion at the Ulyanovskaya mine in 2007 killed 110 people, at Raspadskaya in 2010 - at least 66 people. This is probably why it has already been decided to give Rostechnadzor the right to independently suspend the operation of mines in case of gross violations and to remove from work officials guilty of violating safety rules.
This step, in fact, is a return to Soviet practice, says Ivan Mokhnachuk. “Then the mining technical inspector, who had to spend at least 50% of his working time underground, upon discovering any violation, had the right to immediately turn off the power and stop work. At the same time, he usually put a seal on electrical equipment. Someone broke the seal - court, prison,” says Mokhnachuk. With the privatization of the Russian coal industry in the late 1990s, inspectors lost their status - in particular, they were deprived of their “underground” experience, which allowed them to retire at 50 years old, and their salary began to correspond to the level of a semi-skilled worker.
“Then they were deprived of the right to independently stop the operation of the mine, as part of the fight against corruption. Now this can only be done through the courts, and during this time the mine may simply explode. Many inspectors have long stopped going down into the mine, receiving “envelopes” from the owners. The number of violations accumulated, and then accidents began,” says Mokhnachuk.
The role of trade unions and the wage system
Putin recommended that coal companies and trade unions agree that the permanent part would account for at least 70% of miners' wages. It was precisely the strong dependence of the final salary on production volumes, according to experts, that forced mine workers to neglect safety measures: if the site was closed for some time, it would not be able to fulfill the plan, and, as a result, the miners would receive only half of their usual earnings. According to Mokhnachuk, in the near future the union will be engaged in “developing technology” to implement this initiative of the prime minister.
The US authorities have not come up with such initiatives, since the settlement of this issue in the US is traditionally occupied by industry trade unions, which now comprise more than 90% of workers in the American mining industry. The largest of them, the United Mine Workers of America, was created more than a century ago. However, it is not possible to completely solve the problem in the United States either: as noted in the latest review by the American analytical company CostMine, “the volume of coal production still remains the main criterion when calculating the size of the premium in US coal mines.”
Increased fines for safety violations
The fine that can be imposed on the head of an enterprise in Russia does not exceed 5,000 rubles, for legal entity- 50,000 rubles. In the United States, a mine director can be fined up to $250,000. The miners' union intends to seek increased fines and payments to the families of dead miners. “Today, according to the law, the payment to the relatives of the victims is 64,400 rubles, we will ensure that it is no less than 1000 times the minimum wage, or about 4.5 million rubles,” says Ivan Mokhnachuk.
Technical re-equipment
Despite the fact that the coal industries of Russia and the United States employ approximately the same number of people, America produces several times more coal. In 2009, coal production in the United States fell by 8.5% (the largest drop since 1958) to 1.07 billion tons. Coal production in Russia fell by about the same amount last year to 300 million tons.
Labor productivity, which makes it possible to reduce the number of workers and, accordingly, the number of potential accident victims, began to rise sharply in the American coal industry at the turn of the 1970s and 1980s. This was due to the introduction of new technologies for the development of coal seams, which made it possible to increase coal production simultaneously with a decrease in the number of employees. Only the widespread introduction of longwall mining technology, suitable for mining thick and horizontal coal seams, made it possible to reduce the number of employees at the mining site by almost 10 times. If in 1983 only 20% of all underground coal mines were developed using the “longwall” technology, then by 1995 - already 45%. As a result, miners' labor productivity more than doubled over the same period - from 1.59 tons per hour per worker to 3.85 tons per hour.
The technological lag is connected to a large extent with the issue of employment of released miners in regions where coal enterprises are city- and even regional-forming. “Coal mining in our country is traditionally a very labor-intensive industry, with a large number of workers, entire mining dynasties. As practice shows, such things are very difficult to break; most likely, the process of increasing labor efficiency will be evolutionary,
Microsoft documentation describes five ways to change TCP settings in the registry to make Windows 2000 systems more resilient to Denial of Service (DoS) attacks and other types of attacks. These methods are effective on Windows machines 2000, connected to territorial distributed networks(WAN) and Internet, and on sites with increased security requirements. Making such complex changes requires manually tuning many of the central TCP algorithms, and I recommend making changes to production systems only after experimenting on a test machine. Incorrect or poorly selected TCP/IP settings can negatively impact most services and Windows applications 2000. These techniques affect the low-level algorithms used by the operating system to manage and route messages, so the test system should be connected to multiple subnets with one or more routers.
TCP/IP settings in the registry
All information about the working Windows system 2000 is stored in the registry key HKEY_LOCAL_MACHINESYSTEMCurrentControlSet. The Services subsection of this section, in turn, contains one section for each customizable Windows services 2000 (even for blocked and not installed services). Screen 1 shows general TCP/IP configuration data from the HKEY_LOCAL_MACHINE SYSTEM CurrentControlSet Services Tcpip Parameters section. By default, configuration data for each service is stored in the Parameters section, in a subkey with the appropriate name.
When working with several adapters (both hardware network adapters and software Routing and Remote Access ports), a corresponding subsection for the class identifier of each adapter is formed in the HKEY_LOCAL_MACHINE SYSTEM CurrentControlSet Services Tcpip Parameters Interfaces section. Clicking an adapter's class ID in the right window of Registry Editor displays configuration information for that adapter (Figure 2).
The TcpipParameters section contains elements that define TCP/IP behavior for all interfaces. When you configure an adapter that provides TCP/IP communications, the system copies many of these settings to the Interfaces section of that adapter. If the same element is included in TcpipParameters and in the section of a specific adapter, then you can change the TCP/IP mode of an individual adapter by editing the corresponding parameters. When considering registry changes that can be used to reduce system vulnerability, you should be aware of general settings and settings specific to each adapter.
If the element I mentioned is not in the corresponding section, it should be created. When creating registry elements, you need to pay attention to the correctness of the type and values of the entered data. It is impossible to predict how the system will react (if at all) to incorrect data entry. The changed TCP configuration settings will take effect after the system is rebooted.
Protection against SYN DoS attacks
TCP SYN DoS attacks are a favorite weapon of hackers. Before considering ways to protect against such attacks, it is necessary to understand how TCP/IP works.
When initiating a TCP session on an IP connection, system A sends a synchronization packet (SYN) to system B. System B responds by sending machine A a SYN-ACK packet as an acknowledgment. If System B does not receive an acknowledgment of the SYN-ACK from System A, then the SYN-ACK is repeated up to five times. Having not received a response from system A, system B increases the interval before attempting to send a SYN-ACK again. Thanks to these delays, systems manage to establish connections over slow communication channels.
If system A does not respond, then after a certain time, system B disconnects. The timeout process can take 3-4 minutes because System B must contact System A a certain number of times before terminating the session. When System B closes the connection, TCP releases the resources allocated to the incoming connection. The process of releasing resources may take another 3 to 5 minutes.
In a typical SYN attack, an attacker runs a program on System A that sends multiple SYN requests to System B over a short period of time. Each SYN request is sent in an IP packet containing the IP address of the machine that sent the packet. This address may point to the attacker's machine, but more often a false (spoofed) address points to another computer or a non-existent machine. In either case, System B attempts to send a SYN-ACK to the source address in response to each SYN message. If system A does not respond, then machine B is forced to keep the connection “half-open” and cannot close it without making a certain number of attempts. Obviously, a SYN attack can quickly overload a system.
Windows 2000 machines handle hundreds of simultaneous TCP/IP connections. Once under a SYN attack, the system can allocate up to half of its free TCP/IP resources to service requests from incoming connections. But the process of allocating, managing, and reusing TCP/IP resources ultimately causes the system to hang.
Using the command
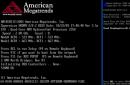
Netstat np tcp
You can monitor a system that may be under a SYN attack. The n switch tells the Netstat command to display addresses and port numbers in numeric form; the p switch displays only active TCP connections. Screen 3 shows a system with many connections in the SYN_RECEIVED (half-open) state. For each connection, the address of the system that supposedly sent the SYN packet is given. If such connections remain in the SYN_RECEIVED state for more than a few minutes, then a SYN attack is likely taking place. Typically, the connection status changes to ESTABLISHED in less than a minute.
 |
| Screen 3. A SYN - DoS attack is in progress. |
Windows 2000 automatically monitors three counters that track the number of active TCP/IP ports and the number of half-open ports to detect potential SYN attacks. If the counters exceed certain thresholds, Windows 2000 assumes that a SYN DoS attack has begun. During a SYN DoS attack, the TCP engine queries the HKEY_LOCAL_MACHINE SYSTEM CurrentControlSet Services Tcpip Parameters section to determine what response action should be taken in this situation. The SynAttackProtect element specifies the number of attempts and the time interval between attempts. These values specify the connection timeout conditions. The SynAttackProtect parameter is of type REG_DWORD and accepts the values 0, 1, or 2.
On systems connected to the Internet, this parameter should be set to 1 or 2. As a result, the number of SYN-ACK packet retransmissions and the interval between them is reduced and, as a result, the time allotted for waiting for normal and false requests is reduced. For the most reliable protection against SYN DoS attacks, set the parameter to 2.
For systems that can be directly accessed from the Internet (especially those not protected by a firewall), the SynAttackProtect element should be set to a value of 1 or 2. Check with the vendor about the firewall's protection against SYN and Ping of Death attacks. Please note that increasing the SynAttackProtect value changes the system's behavior when processing both normal and DoS connection requests.
Protection against Dead-Gateway attacks
When configuring TCP/IP settings manually, you must specify the address, subnet mask, and default gateway. If the system receives a packet with a destination address that is not on the local subnet, the IP engine forwards the packet to the gateway. The gateway then forwards the packet to another router or final destination. A normally functioning gateway always acknowledges receipt of such packets. If the system does not receive response messages for 25% of the packets sent to the gateway, then it considers the gateway down, or “dead”.
To prevent the consequences of a router failure, you can specify multiple routers on the Advanced Settings tab of the TCP/IP Properties dialog box. If multiple routers are selected, Windows 2000 automatically activates a feature that detects the dead router and selects the next router from the list. This dynamic configuration change procedure increases network fault tolerance, but at the same time allows an attacker to redirect network traffic.
There are two registry entries associated with dead gateways. The first, DeadGWDetectDefault, is found in the TcpipParameters section and defines the default dead gateway detection mode. It is used to enable or disable the dead gateway search procedure on all TCP/IP interfaces. If necessary, you can use the second element, EnableDeadGWDetect from the Tcpip Parameters Interfaces adapterclassID section, to enable or disable dead gateway detection for a specific adapter. In dead gateway detection mode, the TCP mechanism instructs IP to use a backup gateway if TCP does not receive a response from the gateway after several attempts to transmit the packet. If discovery mode is disabled, TCP cannot forward packets to another gateway.
To manually enable or disable TCP detection of dead gateways, you must set the DeadGWDetectDefault parameter to 0 (disable) or 1 (enable). For individual network adapter for this purpose, you should add or change the DeadGWDetect parameter in the InterfacesadapterclassID section.
If dead gateway detection is disabled, TCP cannot dynamically redirect packets to other routers if the default gateway fails. Failure to forward packets beyond the local subnet results in the termination of all connections except local ones. For this reason, and also because an attack through a backup gateway is a much rarer event than SYN DoS and Ping of Death attacks, I recommend disabling dead gateway detection only in those areas of the network where particularly strict confidentiality is required .
Protection against PMTU attacks
As can be seen from Table 1, for each physical type of network, for example Ethernet and X.25, a maximum frame size is set, called the Maximum Transmission Unit (MTU) - the maximum size of the transmitted data block. It determines the amount of data that can be transmitted over the network in a single block. When messages cross network boundaries various types(for example, Ethernet and Token Ring), the MTU of the source network can be smaller or larger than the MTU of the destination network.

When a 16 KB network packet crosses a network boundary with an MTU of 1500 bytes, MTU information is exchanged between computers on both networks. The sending machine then breaks (fragments) the message into several packets, each of which is assigned a sequence number that identifies the sequence of small packets in the larger original message.
Packet fragmentation is an important factor in performance degradation. When a packet is divided into several fragments, the transmitting machine consumes processor cycles and memory, enters a sequence number, and transmits the reduced packet. The receiving system consumes processor cycles and memory resources by storing packets in a buffer, ordering packets by number, and reconstructing the frame.
Windows 2000 implements a Path MTU (PMTU) algorithm that detects the smallest MTU on the path between the source and destination of a message and converts the message into packets of the appropriate size. Thus, the PMTU optimization algorithm eliminates fragmentation at multiple routers along the path connecting the source network to the destination network.
During the process of determining the PMTU, the machine becomes vulnerable to attacks. Theoretically, an attacker could program the system so that the MTU determination procedure produces a result of 68 bytes (the smallest size provided by TCP/IP). Windows 2000 uses this value to package and broadcast all network messages to a target system outside the local subnet. The same attacker can then bombard the system with hundreds or thousands of packets. If incoming messages arrive faster than the system can divide them into 68-byte chunks for forwarding to the target machine, all resources on all machines processing the message may be exhausted.
To avoid this situation, you should block the PMTU determination process. You can control the process using the EnablePMTUDiscovery element of the TcpipParameters section. The parameter is of type REG_DWORD and can take the values 0 (“false”) and 1 (“true”). By default, the PMTU discovery process is enabled.
If done intelligently, disabling PMTU detection can prevent an attacker from setting the MTU, and therefore the PMTU, to an unacceptably small value. But at the same time, an important network optimization algorithm is blocked. By tightening the system that routes network messages, the administrator sets the same size (576 bytes) for all packets forwarded to subnets outside the local subnet. The size of such a packet is slightly more than a third of a standard Ethernet packet (1500 bytes).
Protection against common DoS attacks
A system that has initiated a TCP connection with another machine periodically sends a KeepAlive packet, which is simply an ACK message, to the target machine to ensure that the idle connection has not yet been closed. If the target system is still connected, it sends a confirmation message. If the connection is interrupted, no response is received and the transmitting system ends the communication session. By Windows default 2000 disables the KeepAlive feature because this mechanism imposes a significant overhead on resources, especially if the server must query the status of hundreds or thousands of potentially idle connections.
It makes sense to enable the KeepAlive function on machines that provide resources to a limited number of users. To manage KeepAlive requests, two elements of the TcpipParameters section are used - KeepAliveTime and KeepAliveInterval.
A system with KeepAlive enabled sends an ACK packet to the target machine if the connection has not been used for the period of time specified by the KeepAliveTime element. The default KeepAliveTime value is 7,200,000 ms (2 hours). If the remote machine responds to a KeepAlive message, but the connection is otherwise inactive, the source system will send another ACK request after 2 hours.
If the source system does not receive a response, it repeats the ACK request at the interval specified by the KeepAliveInterval parameter. The default KeepAliveInterval value is 1000 ms (1 s). The source system sends up to five requests to the remote system at one-second intervals (the number of retransmissions is determined by the TCPMaxDataRetransmissions element of the TcpipParameters section). If the remote system does not respond after the maximum number of attempts, the source system closes the connection.
The KeepAliveTime value can be reduced from 2 hours to 30-45 minutes to quickly close unused TCP connections and free up resources for other users. Please note that this setting affects all TCP connections, including local connections, so you must carefully consider the implications of this change. To protect against DoS attacks, Microsoft developers recommend reducing the KeepAliveTime value to 300,000 ms (5 minutes). Except in special cases, it is recommended to use the standard KeepAliveInterval value (1 s).
Preventing attacks using NetBT Name-Release
NetBIOS over TCP/IP (NetBT) messages are unauthenticated, so any system, including one used by an attacker, can send regular NetBT packets to any other computer on the network. To organize a name-release attack, a logical error in the NetBIOS name conflict resolution algorithm is used. Typically, Windows 2000 and Windows NT 4.0 detect name conflicts when a machine registers its name on the network after booting. In case of conflict operating system blocks network functions on a machine attempting to register a duplicate NetBIOS name.
By exploiting a logic flaw, an attacker can send a name service datagram to a machine that has already successfully registered its NetBIOS name. The datagram informs the system of a name conflict. Having received the datagram, the system issues a corresponding message, releases the NetBIOS name and stops responding to requests sent to this name. By releasing the registered name, the system loses all NetBIOS functionality and does not allow NetBIOS names to be used to view and access machines. These actions do not affect TCP/IP functionality when accessing systems by DNS name or TCP/IP address.
You can use the Nbstat -n command to check whether a name conflict actually exists. This command displays the currently registered NetBIOS names, with the Conflict flag for the conflicting names.
Windows 2000 stores NetBT configuration information in the HKEY_LOCAL_MACHINE CurrentControlSet Services NetBT Parameters section. The behavior of the NetBIOS name release mechanism is determined by the NoNameReleaseOnDemand element. Microsoft documentation states that the item appeared in the package Windows fixes 2000 Server Service Pack 2 (SP2), but is not present in the NetBTParameters section by default. It must be entered there manually.
NoNameReleaseOnDemand is of type REG_DWORD. The default value, 0, causes the system to release the name immediately upon receiving a datagram from the name service. Setting the NoNameReleaseOnDemand parameter to 1 causes the system to release the NetBIOS name only if a conflict occurs during the name registration process. By activating this function, you can prevent an attack. This technique will be redundant if the adapter that provides Internet connectivity has already disabled the use of NetBIOS names in TCP/IP connections. This method can only be used on Windows 2000 and NT 4.0 machines with security features implemented in SP6a.
Microsoft Security Bulletin MS00-047 (Patch Available for "NetBIOS Name Server Protocol Spoofing" Vulnerability) warns that when NoNameReleaseOnDemand is enabled, many event ID 4320 messages are written to the event log. The system will log a message with this ID number every time upon receipt of a broadcast request to release generic group names. These requests come from systems that have already registered group names and release the names as part of the standard shutdown process. Messages can be ignored.
Maximum security
The techniques described in this article are aimed at special-purpose systems containing confidential information. With their help, you can increase the fault tolerance of systems, but at the same time there is a danger of reducing the speed and deteriorating functionality of the network. After each change, the machine must be rebooted.
Paula Scherik - Windows editor& .NET Magazine and consultant on network planning, implementation and interoperability. She can be contacted at: