This error is related to the installation of CredSSP updates for CVE-2018–0886. The problem is solved by installing the update.
Introduction
Update released March 13, 2018 Windows security CredSSP authentication protocol covering the CVE-2018–0886 vulnerability. A vulnerability in the Credential Security Support Provider protocol (CredSSP) allowed the remote execution of arbitrary code on a vulnerable system.
On May 8, 2018, Microsoft changed the connection security level from Vulnerable to Mitigated and problems began with connecting to the remote desktop via RDP.
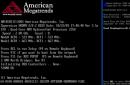
After entering your credentials, an error appears:
An authentication error occurred.
The specified function is not supported.
The error may be caused by a fix to CredSSP encryption
Solution 1: Install the Windows security update on the server.
- Visit the CVE-2018–0886 vulnerability page
- In the Affected Products section from the Downloads column, select the appropriate file, download and install.
Solution 2: Uninstall the Windows security update on the client.
Solution 3: Edit the security policy on the client/server.
It's worth using if you can't connect to the server and install the update. After installing the update, the policy must be returned to its original state.
Open the Local Group Policy Editor:
- Press Win+R
- Type the command gpedit.msc and press Enter
Change security settings:
- Computer Configuration > Administrative Templates > System > Credentials Delegation
- Open the Encryption Oracle Remediation option
- Select "Enabled".
- Set the protection level to “Leave vulnerable” (“Vulnerable”).

The policy has 3 options:
- Vulnerable – clients can connect to vulnerable machines.
- Mitigated—clients cannot connect to vulnerable servers, but servers can accept vulnerable clients.
- Force Updated Clients – safe level customer interactions.
If the client machine does not have a Local Group Policy Editor, the changes are made to the registry.
Article content:
After May 8, 2018, many operating system users Windows systems encountered a problem as a result of which, when trying to log into another Windows computer via remote desktop (or using remoteapp), they receive the following error:
An authentication error occurred.
The specified function is not supported
The error may be caused by a fix to CredSSP encryption.
General information

Screenshot with error text
In this article we will look at 3 ways to fix this error. The first method is the most correct and is what you should use if you encounter this problem. The second and third methods, although they allow you to remove the error, should be used only if it is not possible to install the patch.
Method 1: Install an update to fix CreedSSP encryption
The cause of this error is that the CVE-2018-0886 update is missing on the server side or on the computer you are trying to connect to using Remote Desktop (RDP). To eliminate it, simply install this update on the computer that acts as a server. You can download the update for the required OS version using the links below:
Method 2: Disable CreedSSP encryption error notification through Group Policy
If it is impossible to install updates for some reason, you can disable this error notification. To do this, on the computer that acts as the client, we perform the following steps:

Method 3: Disable CreedSSP encryption error notification by editing the registry
If your edition of Windows does not have a Group Policy Editor (for example, Windows 10 Home), then you will have to make the necessary changes to the registry manually. To do this, on the computer that acts as the client, we perform the following steps:
- Open the registry editor and go to the following path: HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System\CredSSP\Parameters
- Looking for a parameter DWORD called AllowEncryptionOracle, and set the value 2 . If there is no such parameter, then create it.
- Reboot the computer
For those who don't want to mess with the registry, just run the command below in command line with administrator rights:
REG ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\CredSSP\Parameters /v AllowEncryptionOracle /t REG_DWORD /d 2
On March 13, Microsoft published a description of the CVE-2018-0886 vulnerability in the CredSSP authentication protocol, which is particularly used when connecting via RDP to terminal servers. Microsoft later published that it would block connections to unpatched servers that have this vulnerability. As a result, many customers have encountered problems connecting via RDP.
Specifically, in Windows 7 you may see the error: "An authentication error occurred. The specified feature is not supported"
In Windows 10, the error is described in more detail, in particular it says “The error may be caused by a fix to the CredSSP encryption”:

To bypass the error on the client side, many advise disabling Group Policy by setting the value Encryption Oracle Remediation V Vulnerable:
using gpedit.msc in Computer Configuration / Administrative Templates / System / Transfer of credentials, on the left select “Fixing the encryption oracle vulnerability” (funny translation, of course), set “Enabled” in the settings and select “Leave vulnerability”.

or through the registry (since, for example, in Windows Home no gpedit.msc command):
REG ADD HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System\CredSSP\Parameters\ /v AllowEncryptionOracle /t REG_DWORD /d 2
BUT! There is no need to do this! Because Thus, you leave vulnerability and risks of interception of your traffic and other confidential data, including passwords. The only time this might be necessary is when you have no other way to connect to the remote server at all other than via RDP to install updates (although any cloud provider should have the ability to connect to the server console). Immediately after installing the updates, the policies must be returned to their original state.
If you have access to the remote server, then, as a temporary measure, you can disable the NLA (Network Level Authentication) requirement, and the server will stop using CredSSP. To do this, just go to System Properties, on the tab remote connections Uncheck the corresponding box "Allow connections only from computers running Remote Desktop with network level authentication":

But this is also the wrong approach.
The correct approach is to just install necessary updates on the operating system, closing the CVE-2018-0886 vulnerability in CredSSP, both the server one to which you are connecting and the client one from which you are connecting.
List of updates for all operating systems, starting with Windows 7 and Windows Server 2008 available at: https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2018-0886
Select the desired version of the operating system, download the appropriate update from the catalog, install and reboot. After this, the error should disappear.
For example, on Windows Server 2016 the download link will be like this:
Windows OS owners know that the developer provides mandatory support for its operating systems for a certain time. Most often this is because Microsoft periodically releases updates that either automatically or manual mode transferred to a computer and installed there.
Unfortunately, sometimes this leads to not the best consequences. Yes, such updates solve certain problems, but sometimes they create new ones.
For example, installing the KB4103718 package, according to the observations of many users, leads to the fact that an attempt to connect to the server using the RPR remote desktop does not work, but only causes a message on the screen: an error occurred during authentication - the specified function is not supported.
Naturally, this cannot suit a person, who is thus deprived of some of the functionality he needs and is very important. What should I do? Of course - fix it.
So, if Windows 7 RDP authentication failed, then most simple solution there will be a return to the operating system update center and the removal of recently installed packages. As practice shows, this action is quite enough to get rid of the failure.
True, there are several “buts”:
- Next time automatic update everything will come back.
- If you prevent Windows from running such functionality, then operating system may turn out to be extremely vulnerable, since it will not be able to receive the most important protective developments from developers.
Therefore, it is necessary to look for alternative solutions. Experienced users, when asked “An authentication error occurred” - how to fix it, recommend the following actions:
- Install all the most important, latest update packages not only on your equipment, but also on the computer and server to which the user plans to connect remotely via this protocol. This is practically the only and complete solution to this problem. All others are only temporary.
- You can deactivate NLA or provide access to a remote server with a so-called insecure version of CredSSP.
How can you stop using NLA? The following steps must be followed:
- Go through the control panel to all elements, then to the system.
- Open the “Properties” window and go to the “Remote Access” tab.
- At the very bottom you can see a line that begins with the words “Allow connections only from computers...”. Uncheck the box next to it.
After installing the May security updates (dated May 8, 2018 on Windows 7/8/10 platforms and server platforms on Windows Server 2008 R2 / 2012 R2 / 2016), users do not gain access to the remote machine via RDP and RemoteApp, and the following occurs error:
Screenshot: CredSSP error window after making an RDP connection to the server from the client machine.In early spring 2018, Microsoft released an update that prevented remote code execution using a vulnerability in the CredSSP protocol, and in May an update was released after installing which by default, client machines are prohibited from connecting to remote RDP servers with a vulnerable version of the CredSSP protocol. Accordingly, if spring updates are installed on clients, but not installed on servers running Windows Server OS, then we will receive an error when connecting:
"An authentication error occurred. The specified function is not supported. The error may be caused by a CredSSP fix."
Or the English version:
"This could be due to CredSSP encryption oracle remediation."
RDP client error appears after installing security updates:
- Windows 7 / Windows Server 2008 R2 - update KB4103718
- Windows 8.1 / Windows Server 2012 R2 - update KB4103725
- Windows 10 1803 - update KB4103721
- Windows 10 1709 - update KB4103727
- Windows 10 1703 - update KB4103731
- Windows 10 1609 - update KB4103723
- Windows Server 2016 - update KB4103723
To restore the connection, you can simply uninstall the above updates, but this action will open the found vulnerability, so the action plan to solve the problem will be as follows:
- We will temporarily remove the security notification that blocks the connection on the computer from which we connect via RDP;
- Let's connect to it via the already restored RDP connection and install the necessary security patch;
- Let's turn back the security notification that was temporarily disabled in the first point of the action plan.
- Open the local group policy editor: Start - Run - gpedit.msc;
- Go to the section Computer Configuration - Administrative Templates - System - Credentials Delegation - English;
- We find a policy named Encryption Oracle Remediation. Enable the Enabled policy and select Leave Vulnerable as an option in the drop-down list;
 Screenshot: Enabling GPO Option - Fixing Encryption Oracle Vulnerability
Screenshot: Enabling GPO Option - Fixing Encryption Oracle Vulnerability
- All that remains is to update the policies on the computer (to do this, open Cmd and use the gpupdate/force command) and try to connect via RDP. When the policy is enabled, client applications that support CredSSP will be able to connect even to unpatched Remote Desktop servers.
If this home computer If you have a stripped-down version of Windows and you don’t have access to the Local Group Policy console, it doesn’t matter, we’ll use the registry editor (Regedit). Let's launch it and follow the path:
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\CredSSP\Parameters
and set the AllowEncryptionOracle parameter value to 2 (0x00000002).
Then, you need to download and install security updates suitable for your system (I am publishing direct links to updates for Windows Server for your convenience, which I highly recommend installing):
- Windows Server 2016 / Windows 10 1607 - KB4103723
- Windows Server 2012 R2 / Windows 8 -